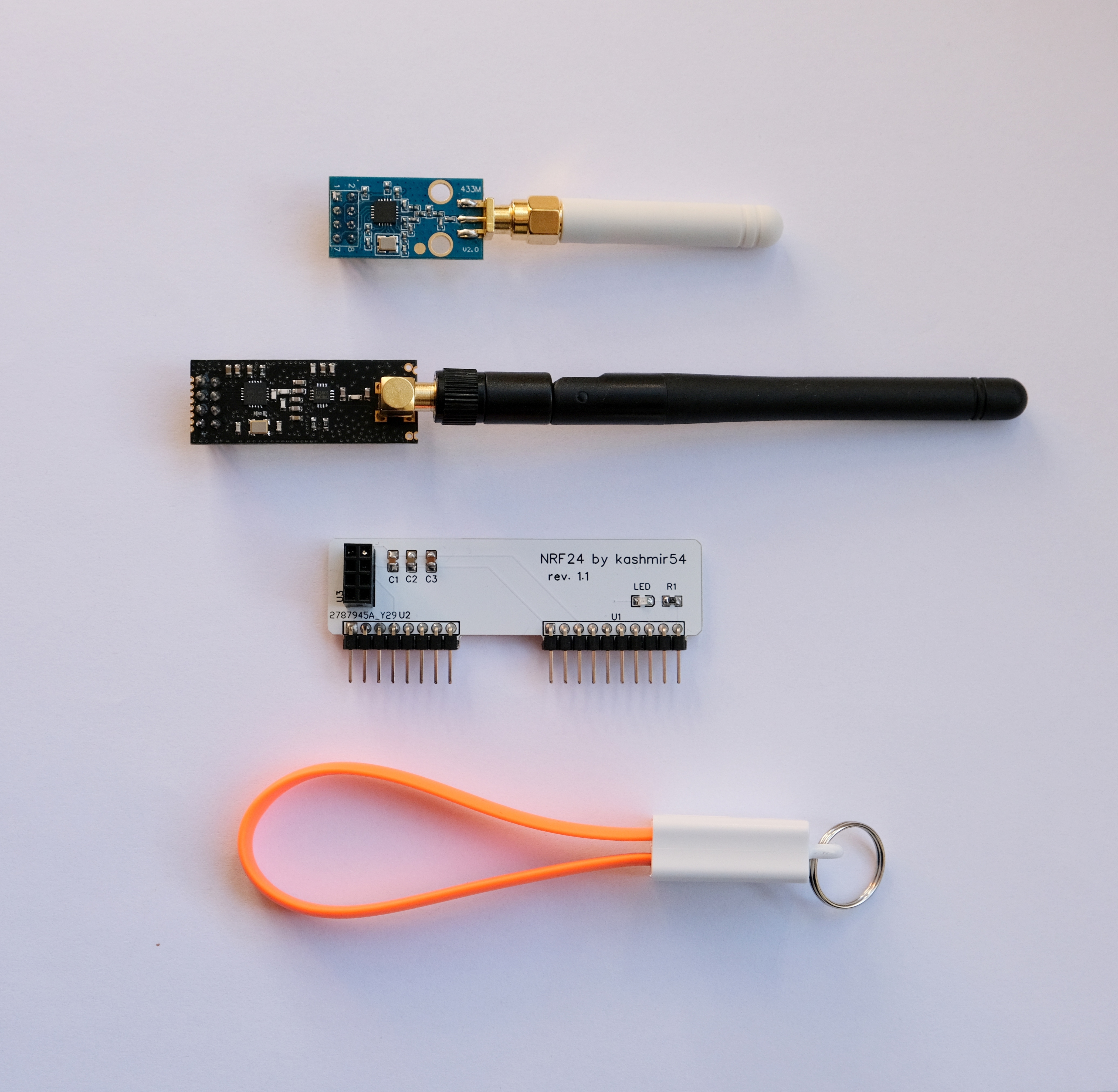
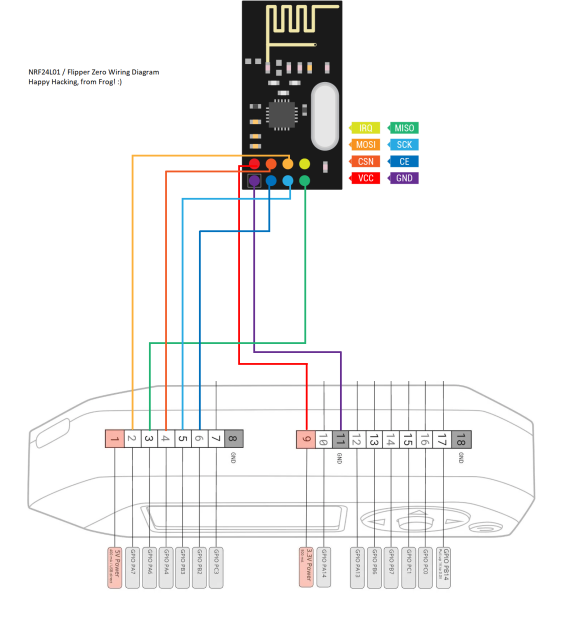
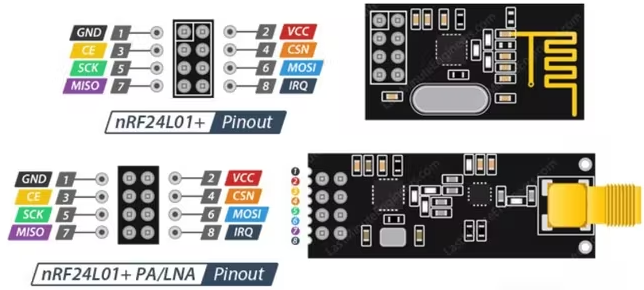
NRF24
This module operates on the 2.4GHz band, which allows the user to interact send, and receive data in that band. Unlike the ESP32 (which also operates on the 2.4GHz band) this chip does not implement the TPC/IP stack, therefore, control of the raw physical layer is provided. This module is used by Flipper’s GPIO plugins such as MouseJacker. This plugin is used in combination with the NRF24 Sniffer, which allows us to grab interesting information from devices working in this band.
Probably you already know which devices use this band, that’s right, wireless keyboards and mice, well, some of them. There are some well-known brands and models that implement “unencrypted” packets to communicate the device with the USB dongle, therefore, we can sniff the spectrum to grab the address of the device and then use it to send our curated payload to the dongle. Further information can be found in the original blog post or in mousejack.com.
What implies this vulnerability? Mainly, we can impersonate the keyboard or the mouse and send HID codes, aka, keystrokes or mouse movements. Known products affected by this vulnerability can be found in the JackIt repo. You can check them out and play around with them.
I have developed some PCBs to connect this module. I added some decoupling capacitors for stable power delivery and noise reduction on the signal. Here you have some photos of the PCBs in action:


CC1101
CC1101 is an RF transceiver that works on the sub GHz frequencies. It works on 300-348Mhz, 387-464Mhz, and 779-928Mhz specifically and you can use it on your flipper as an external module for the SubGHz application. With the corresponding antenna, this module allows the researcher to reach further transmission distances (up to 500m), with is a major improvement over the stock Flipper Zero antenna.
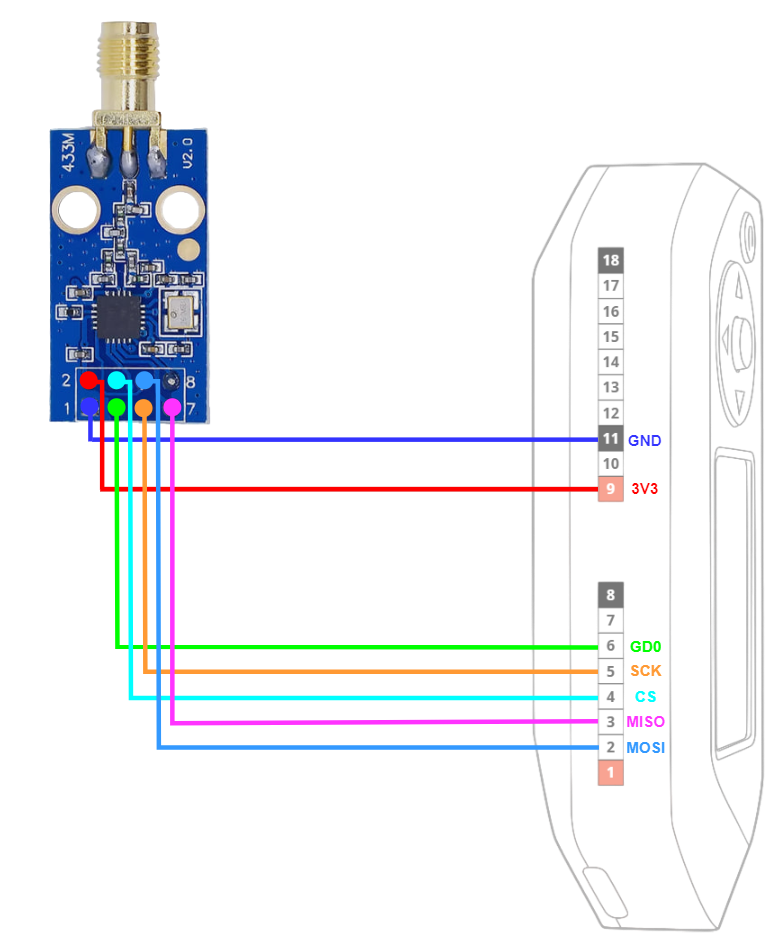
The board that I’ve designed has the same pinout required for the Unleashed SubGHz application to use the external module, therefore, you can use the same board for the NRF24 and the CC1101!
Some tests that I performed at home, showed that the stock SubGHz module could grab a 433MHz keyfob at 5 meters distance while with the external module I could grab the keyfob up to 20 meters, which is a great improvement. I will arrange more tests in order to get some accurate measurements about this performance.
Here you have the CC1101 external module in action with the same PCB:


3D printed case
Thanks to James Martin, you can now print your own 3D case for the NRF24 board. Find it in the following link. Looks pretty dope!
Megapacks and combos
I also have other interesting stuff, such as USBC keychains, which comes pretty handy on ground pentest operations and have the same orange tone as the flipper do! These gadget allow the researcher to bring the Flipper Zero and the keychain attached without the worry of bringing a spare USBC cable. A perfect combination for the Flipper! I created a “MegaPack RF” which is a combination of all these items, for beginners (and also experienced) FlipperZero users to explore new boundaries for this outstanding tool.