GrabCON CTF 2021

Welcome! I’ve participated on CTF for team ISwearIGoogledIt and got some challenges! I focused on OSINT and Forensic.
Challenge index:
OSINT
Forensic
Web
Crypto
Table of contents generated with md-toc
OSINT
Victim 1
150 We got to know our victims is hiding somewhere. We got access to live CCTV camera of that place. Can you find zip code of that location?
GrabCON{zipcode}
On the live camera we can see a building on contruction or being reformed:


From IP geolocation lookup we can see a hint of its location:
IP Address Country Region City
31.207.115.133 Italy Trentino-Alto Adige Brunico
The city is set to 39031 zipcode, but could be different depending on the part of the city. To make sure of that, we can see that in the photo there is a yellow cableway. On Google Maps we can see that the cableway is on the south of the city and still has the 39031 zipcode:
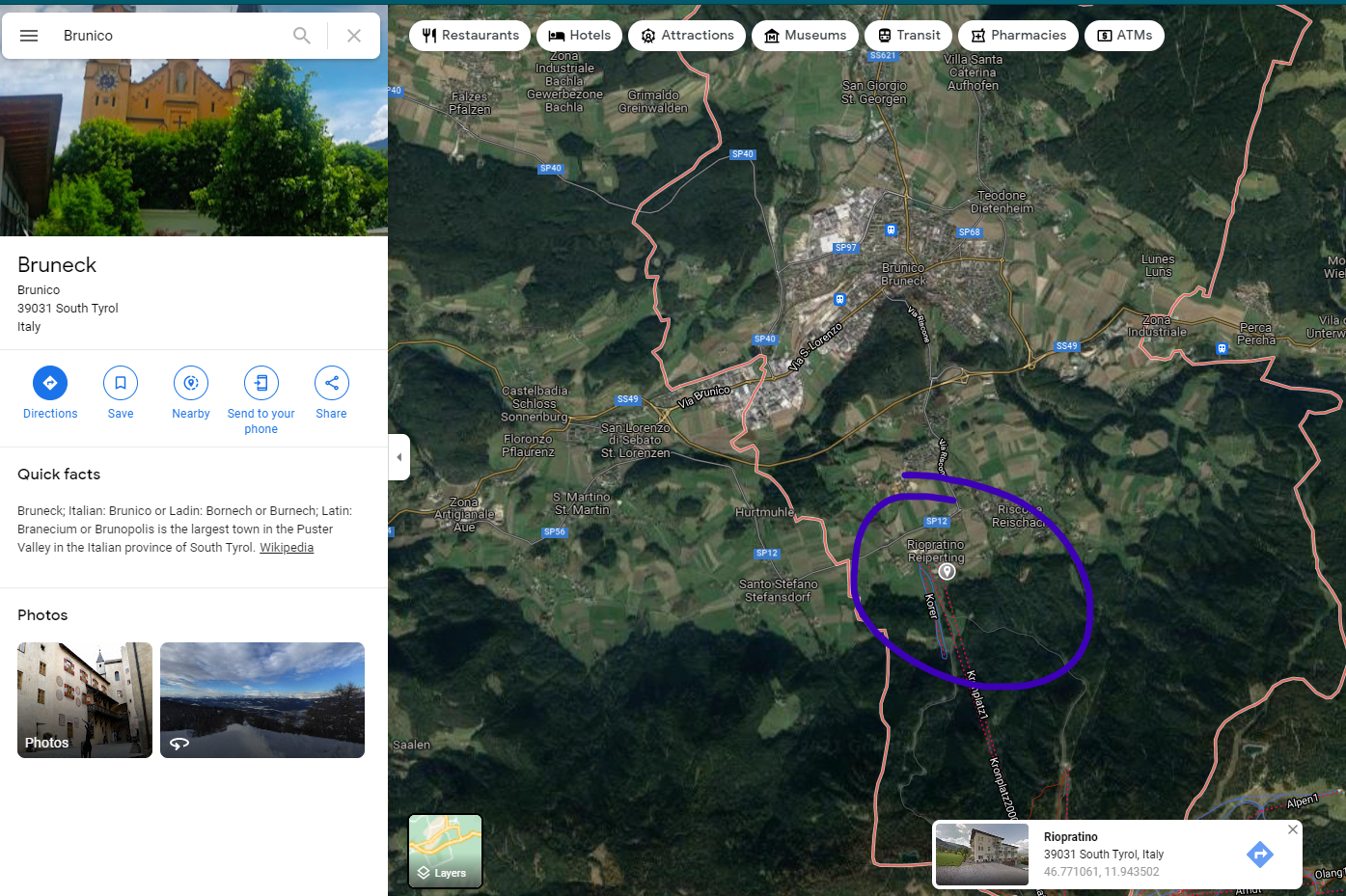
GrabCON{39031}
Victim 2
We’ve managed to get into that place in Trentino-Alto Adige, but we saw a diary left behind in that place owned by him. Go throughing that diary we’ve got this photo. Locals said it was a sceneric view of a mountain from a hotel. Can you find the location of the hotel located near to this place?
File
GrabCON{hotelnameinlowercase}
Author: CETACEAN
They provide us the following photo:

A quick analysis let us with the following clues:

- In Trentino-Alto Adige (challenge description and previous challenge)
- In the photo we can see the word Schennerhof in a building (purple)
- A tower/monument with a clock (orange)
Let’s locate the village. First, I looked for the Schennerhof in Trentino-Alto Adige in Google Maps and found it a place called Schenna:
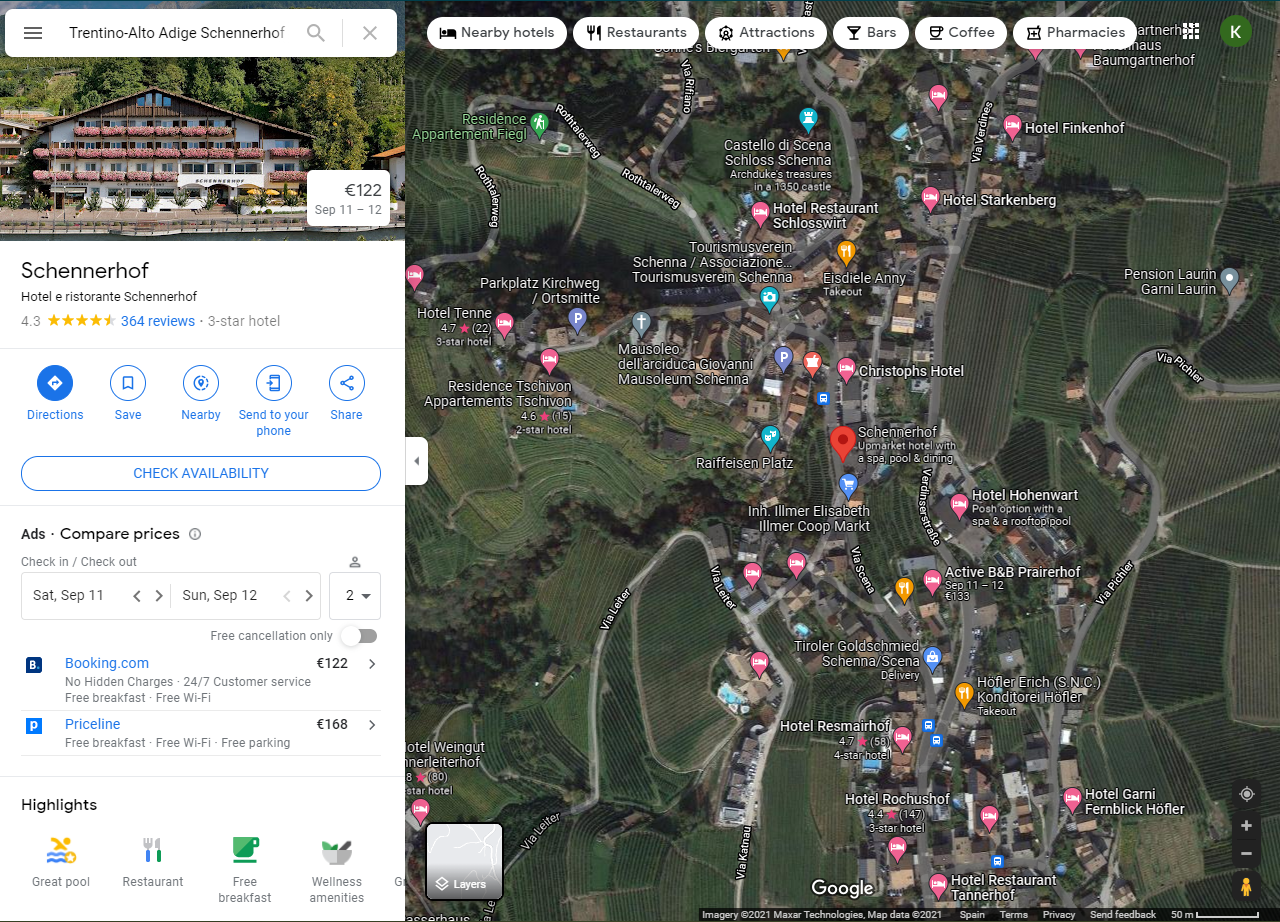
The I looked for the tower name and seems like its the Schloss Schenna
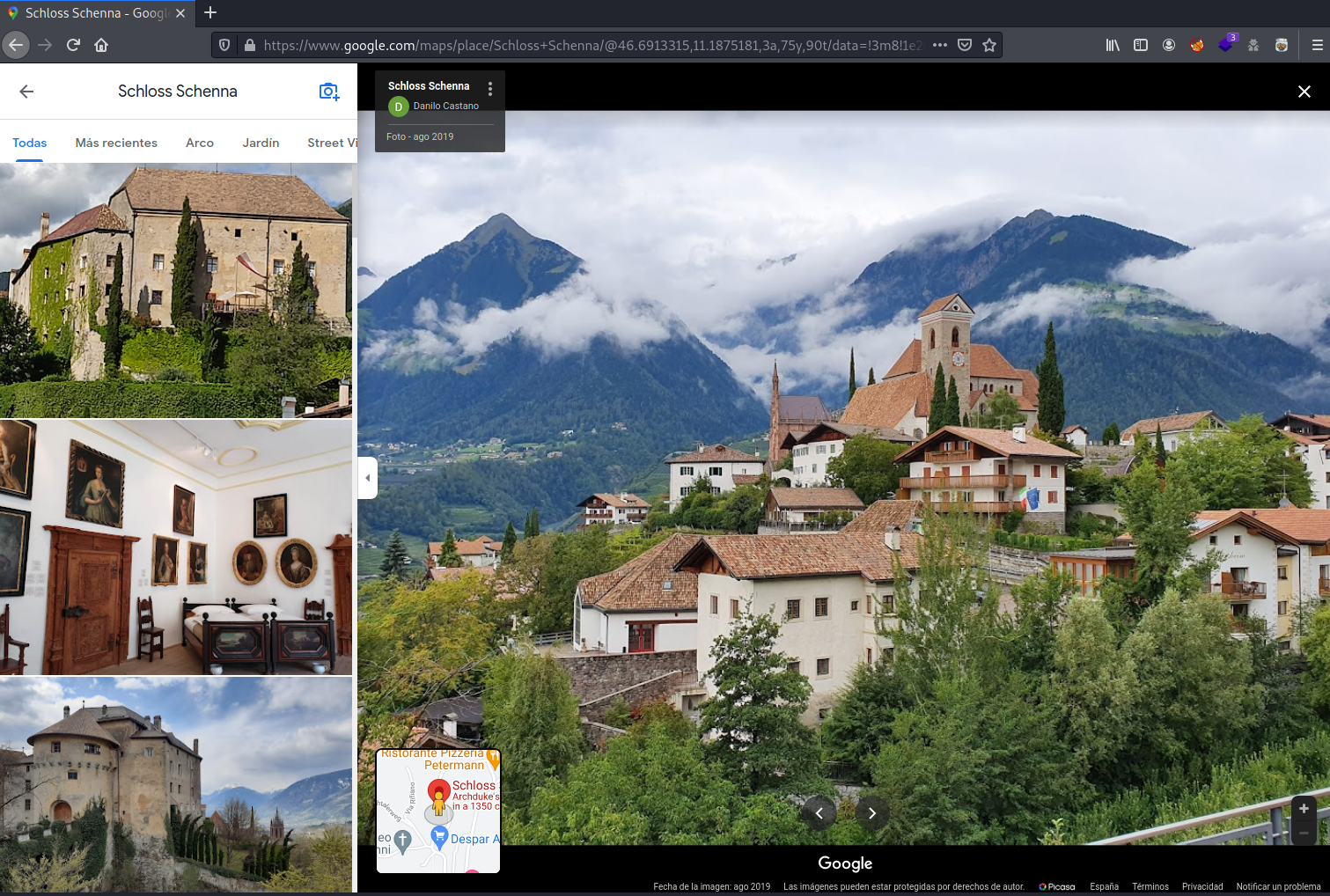
Now that we have located the two elements in the photo, let’s try to retrieve the perpective:
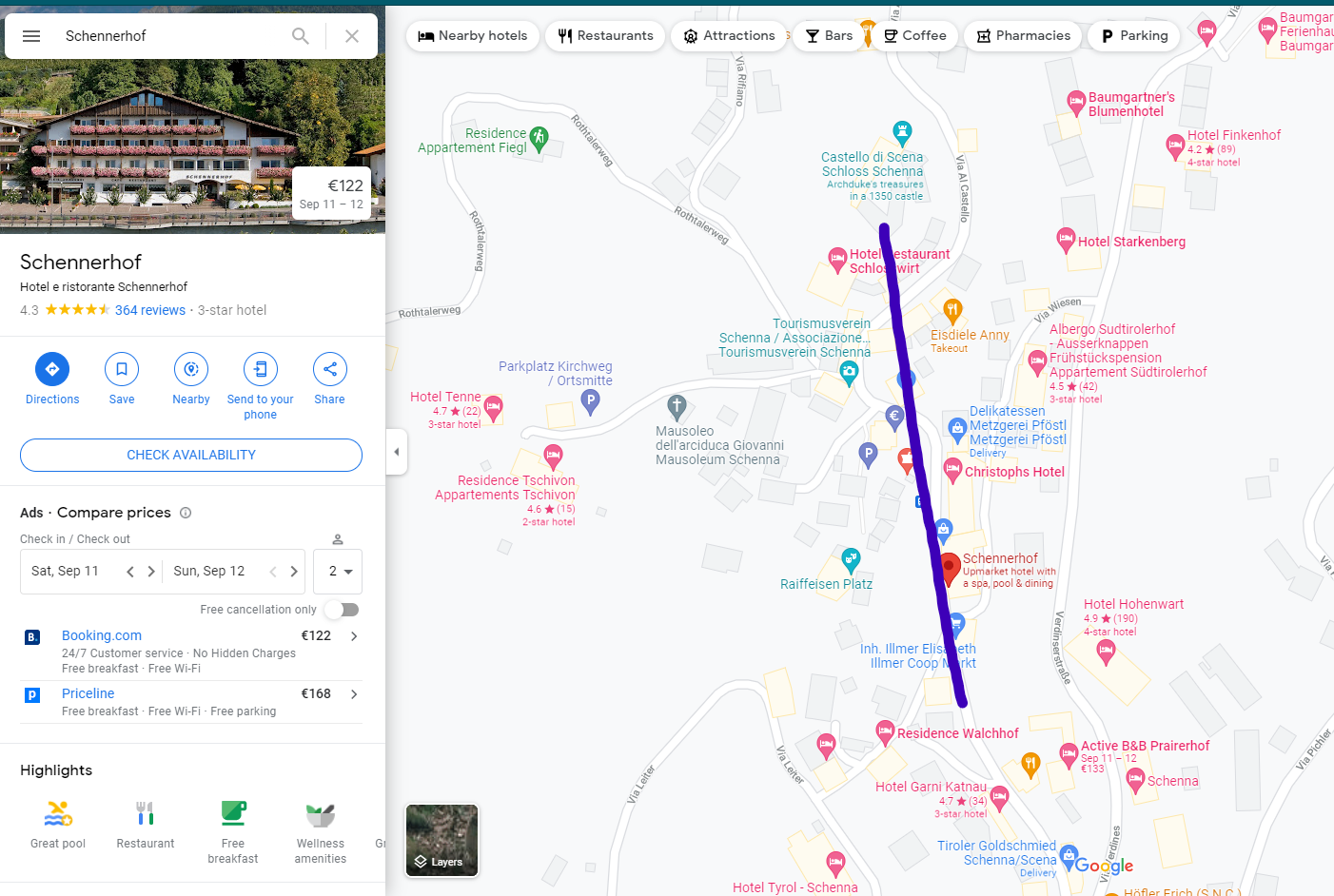
Check this view align with the elements in the photo… Seems like its so close to this place:

Behind of that point, we can see the Hotel Hohenwart, but trying the flag didn’t work…
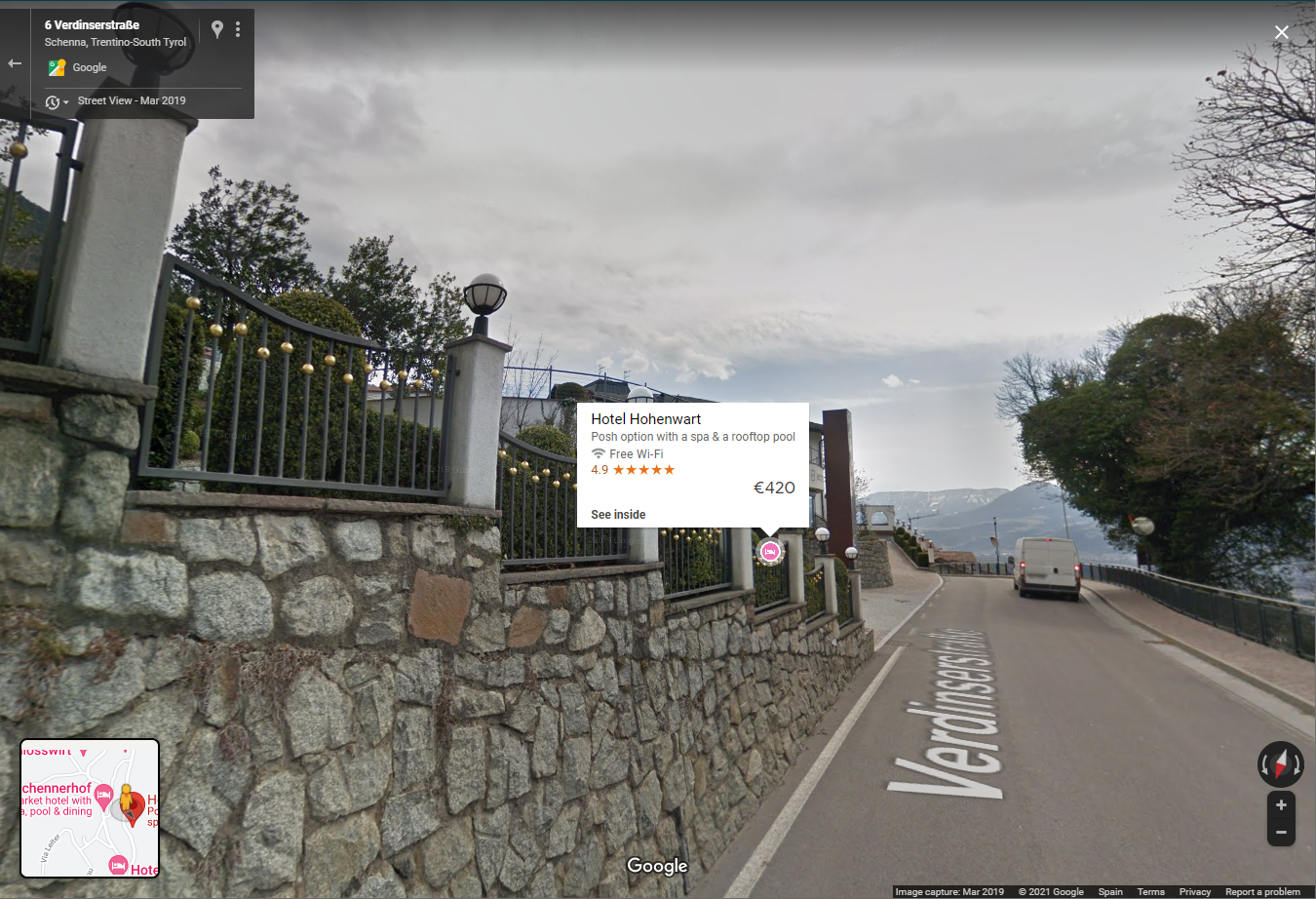
Then I just start thinking about the perpective and checked the reviews and photos from some apartments in the sourroundings of my calculated location. Check the following photos taken from the Apartments Prairerhof:

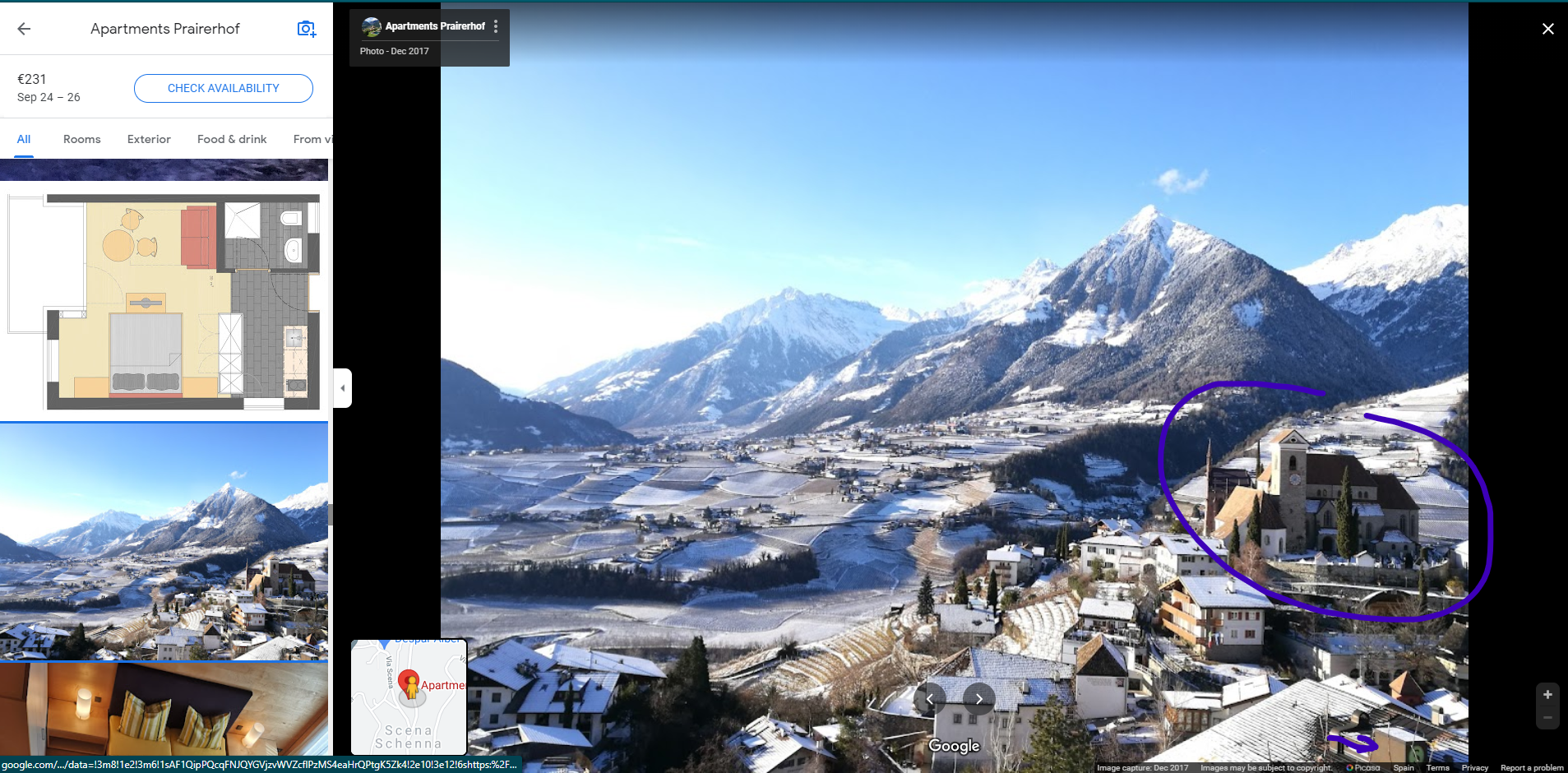
No it couldn’t be from the Apartments Prairerhof, those reviews photos are taken a little bit to the left of out reference photo… I recalculate the perspective with the points in the reference photo:

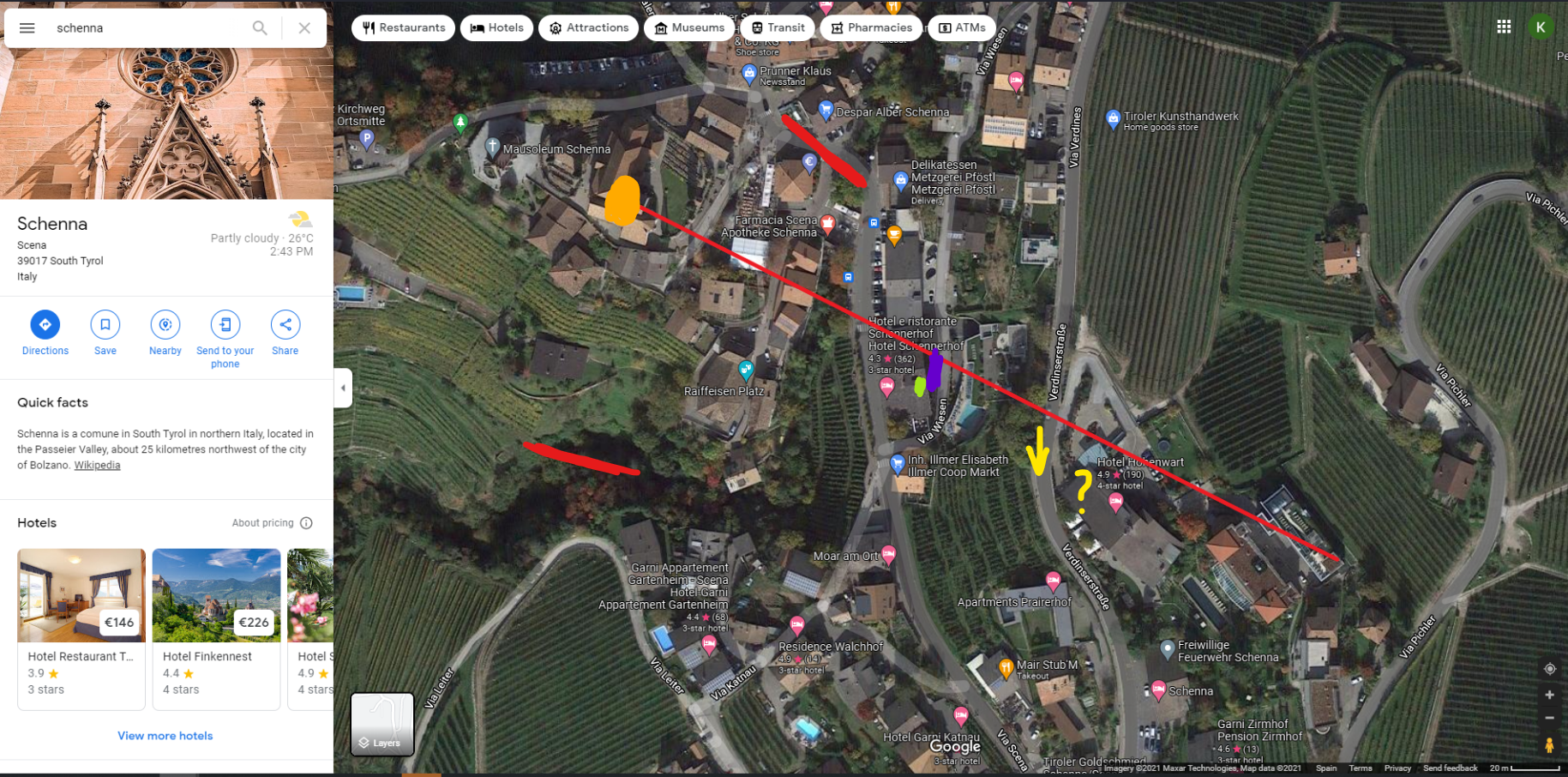
It has to be taken from that purple arrow or from the Hotel Hohenwart for sure:

And yes, they fixed the challenge and the flag worked:
GrabCON{hotelhohenwart}
The Tour(1)
374 w0nd3r50uL! I know her but she did something horrible! She recently switched to some free and open-source software for running self-hosted social networking services. Check out her profile and find the last location she visited when she felt hungry?
I started by looking for the username in Google:
https://www.reddit.com/user/w0nd3r50uL/
Reddit profile is not available. Maybe is on wayback machine?
https://web.archive.org/web/20210904191920/https://www.reddit.com/user/w0nd3r50uL/
Nope.
Then I executed Sherlock:
https://mastodon.social/@w0nd3r50uL
Great, the mastodon profile is real. We can see her photo and some kind of tweets:
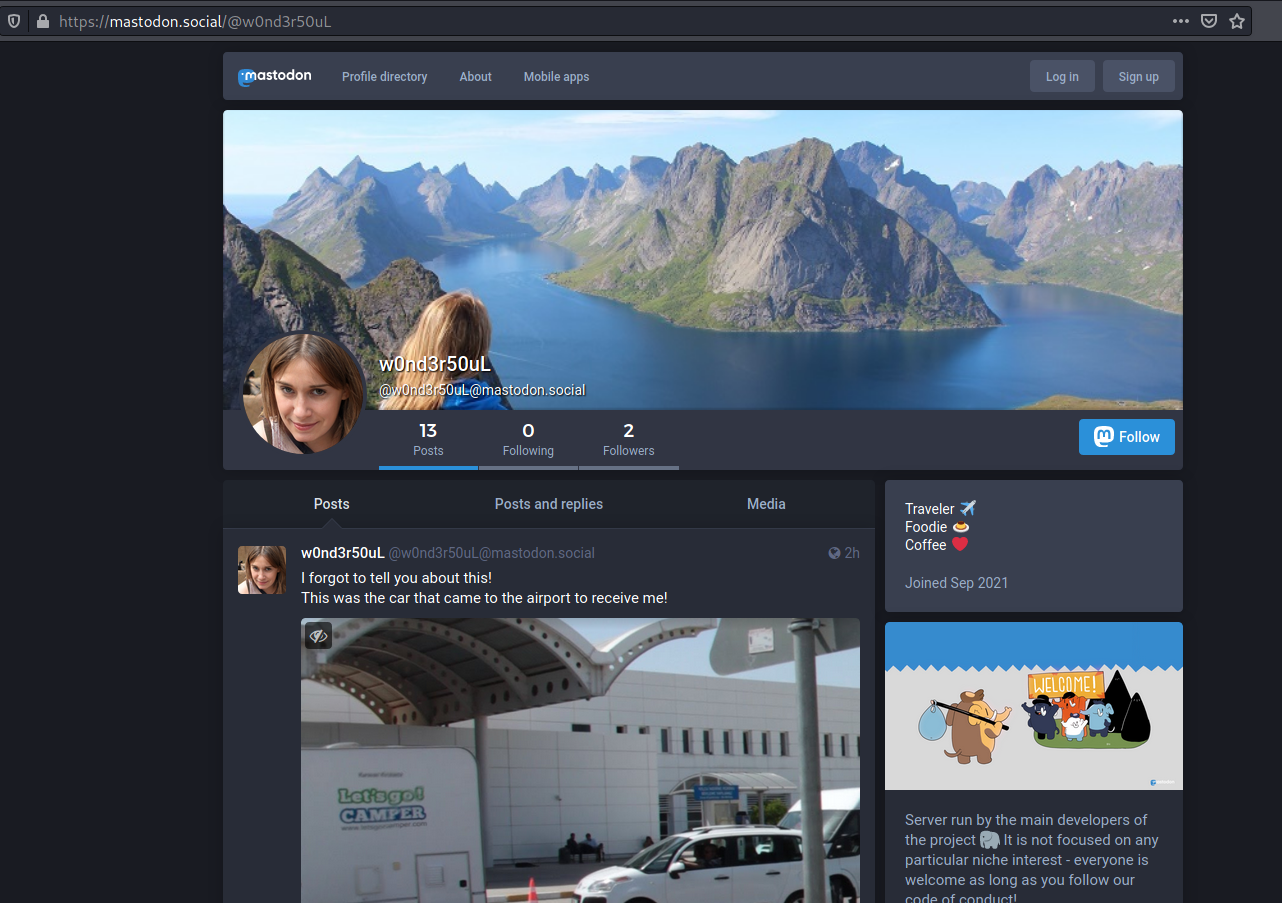
The challenge is asking for a place where she ate:
So she was at Belgrade, Serbia because of the flight pass exposed on a photo (yes, we solved the Tour 2 chall before the 1 ^^’).

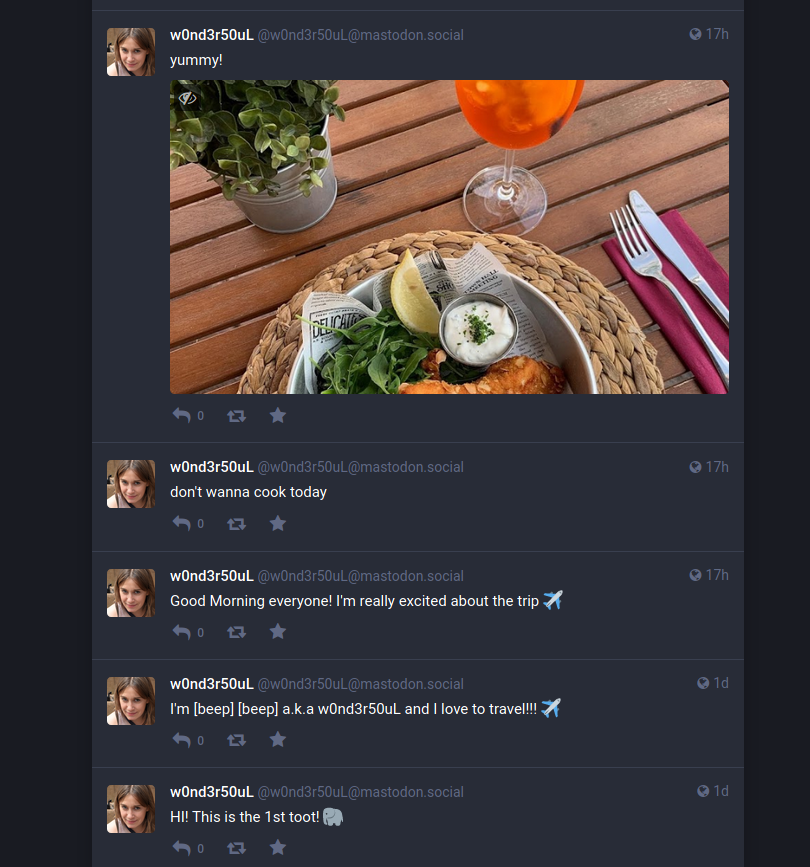
Now things started to get hard. We analyzed the photos on his social media from a restaurant and the photo of the food:


Clues we have until now from the photos:
- A restaurant in the riverside.
- A wide river in Belgrade (Danube).
- Wood chairs at most and some metal ones.
- Little plants on tables and table wooden pads.
- Maybe second lane of buildings since there is another row of buildings in front.
- Tall chimeney holded by metal cables.
- Greenland in the other side of the river.
- Hanged light bulbs in the terrace.
Using Google Lens or reverse search didn’t worked for me. So it was time to look for other posts. This blurred image shows a tower at the bottom. I had some clues for that tower in Belgrade by searching for it at Google with keywords danube belgrade tower:

RazviOverflow came in and worked on finding that blurry tower and got its location and name:

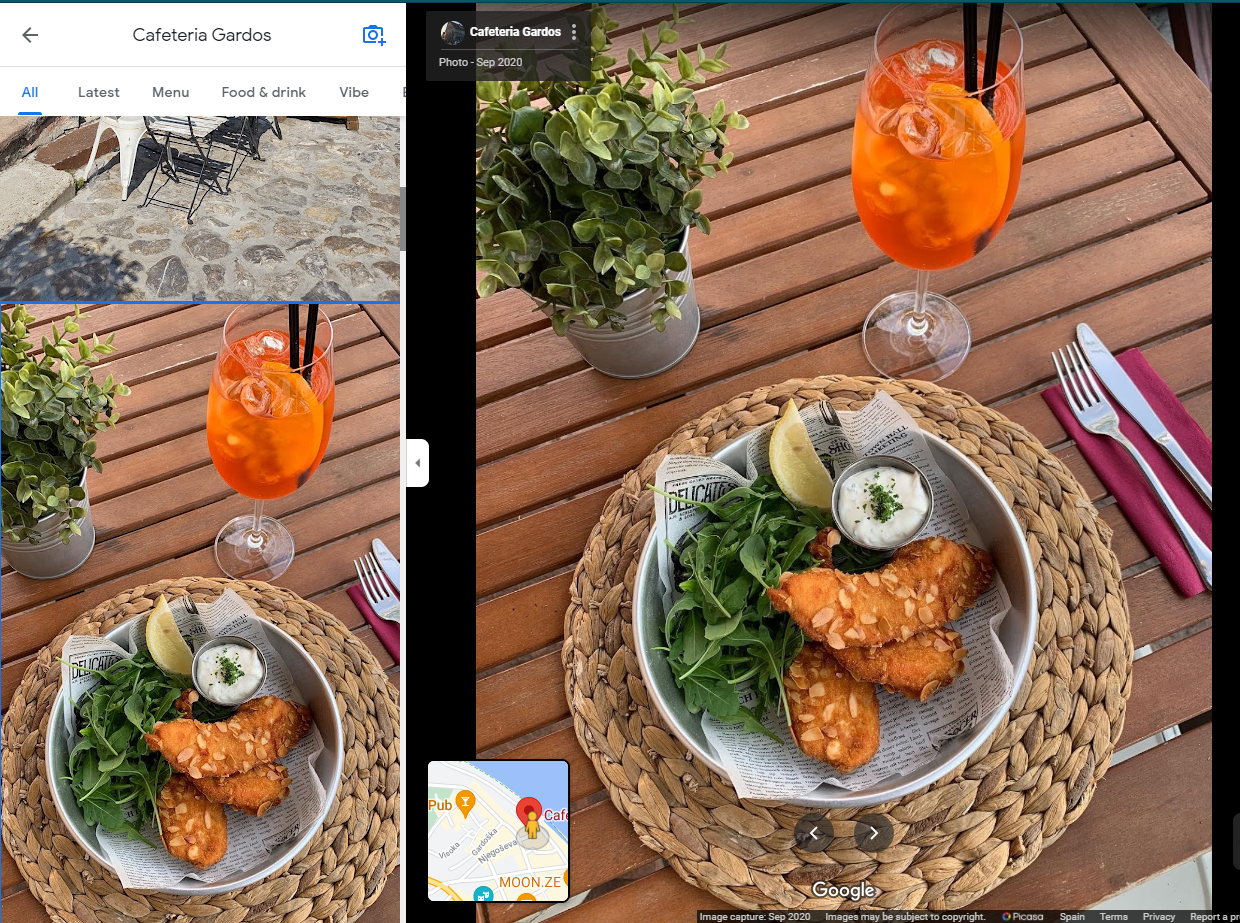
Then I started looking around in that place for the different restaurants, key point here is that the photo shows that it’s a place in second row of the riverside:
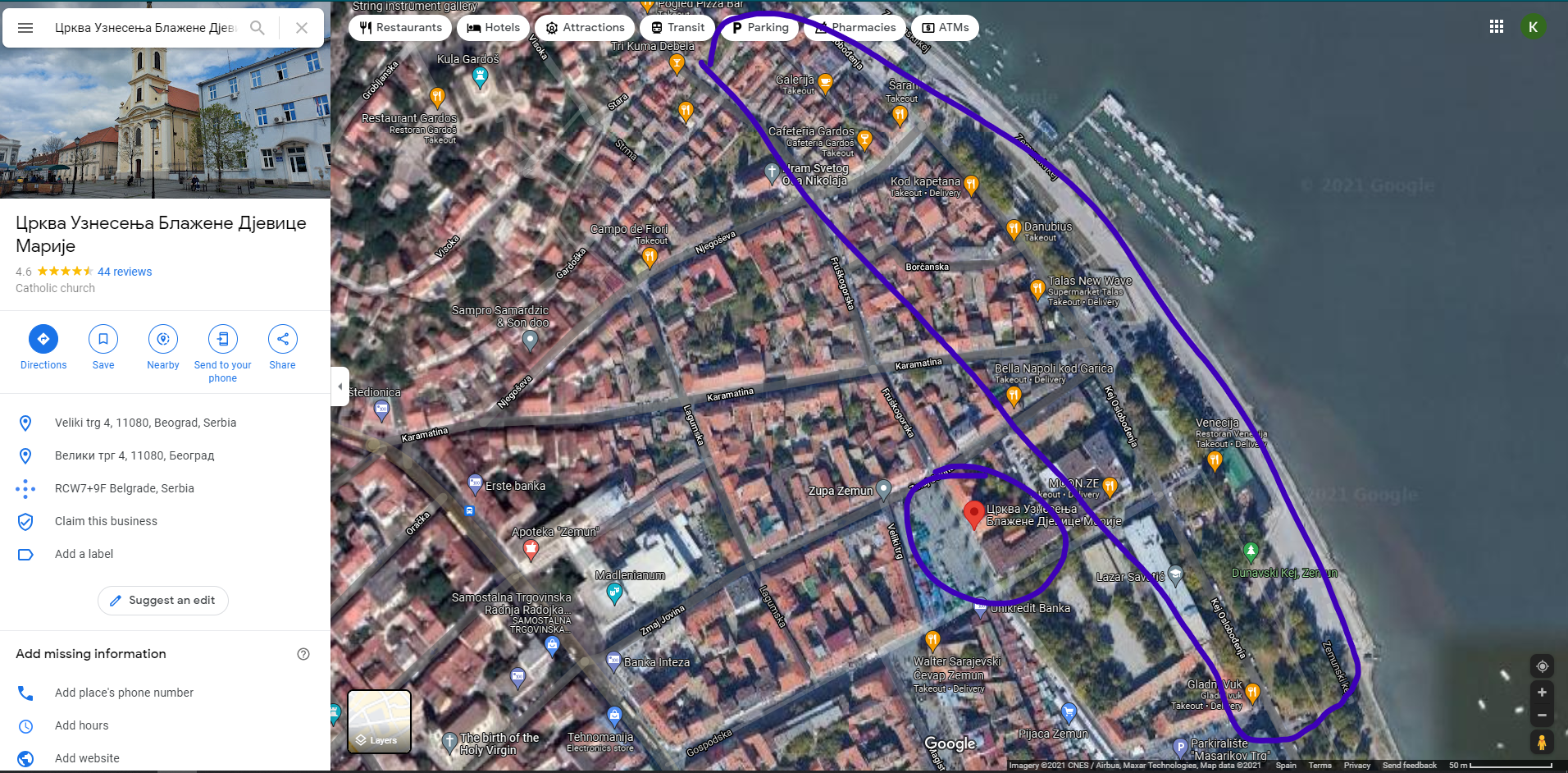
One by one, with the analysis we did at the beginning, looking at the first photo of each restaurant, I came across Gardos Coffee and check out the details in the photo, those chairs look familiar to me:
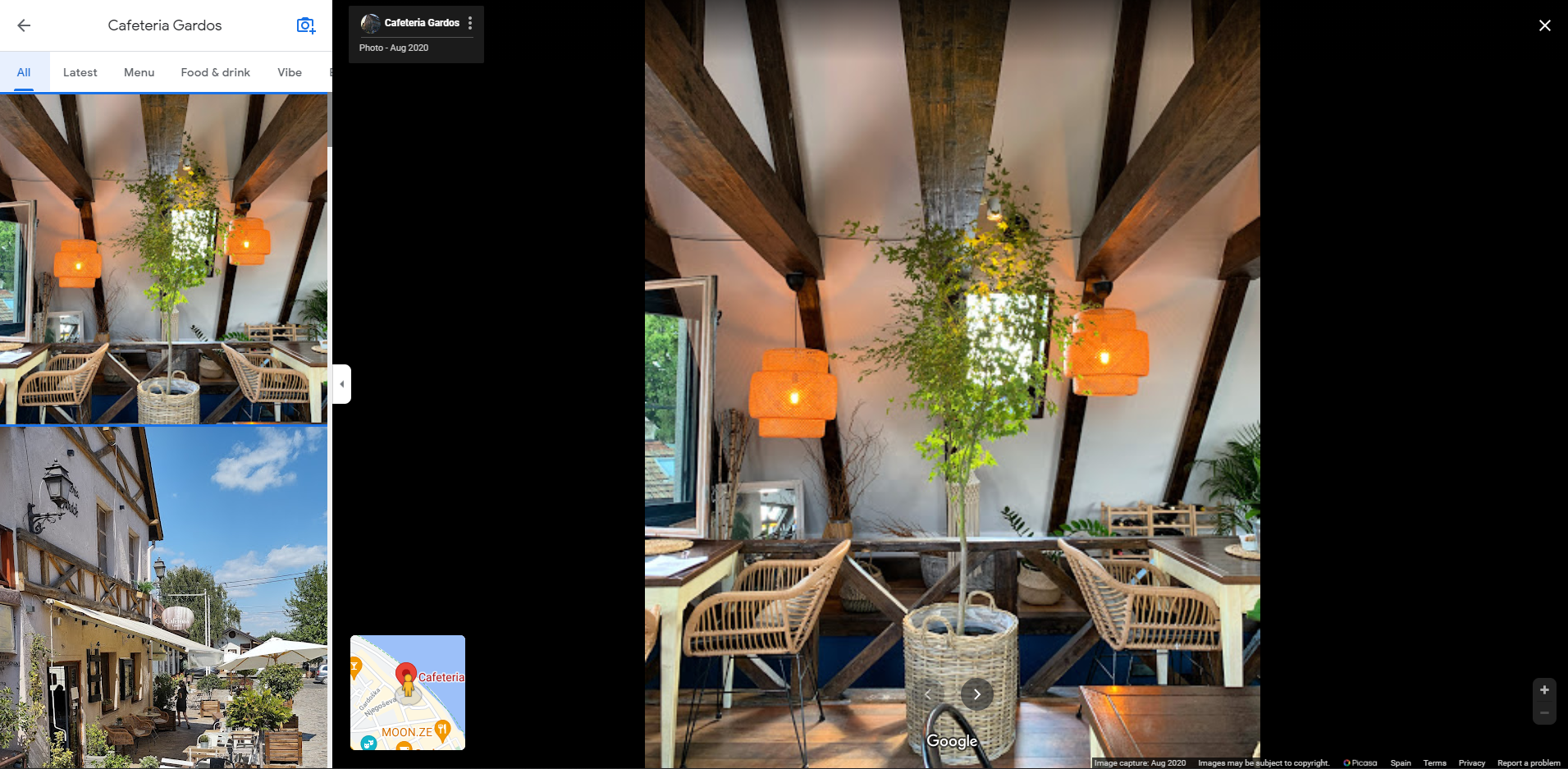
Woooo-wooo, mate, that is the photo she posted on social media, flag if close:
Then on the reviews we find the flag, great challenge:
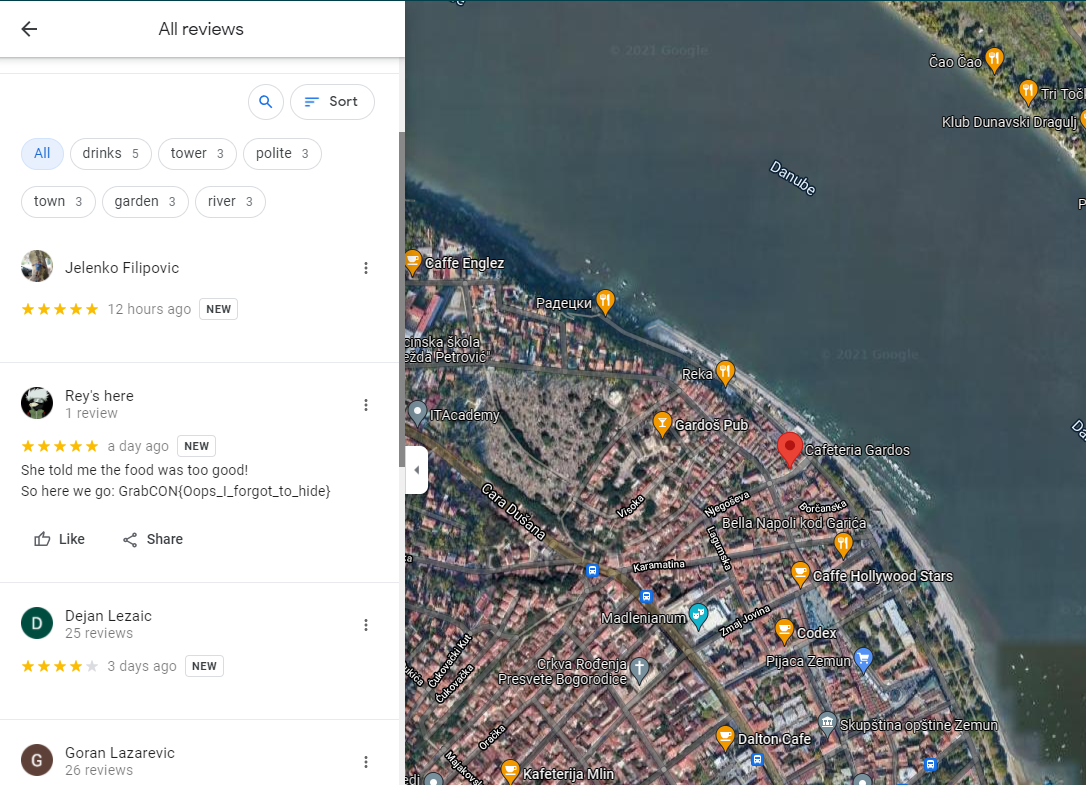
GrabCON{Oops_I_forgot_to_hide}
The Tour(2)
488 Can you find the flight number and the flight operator of the last flight that took her to the final destination? E.g. GrabCON{AF226_Air_France}
On social media we found the flight pass:

We can see that she redacted the information, but forgot the barcode… It’s PDF417 as shows in the cognex website that I use for these things.
Then I cropped the barcode, some adjustments on photoshop and ready to dance:

I used the cognex website but didn’t worked, so an alternative is this online tool to decode it.
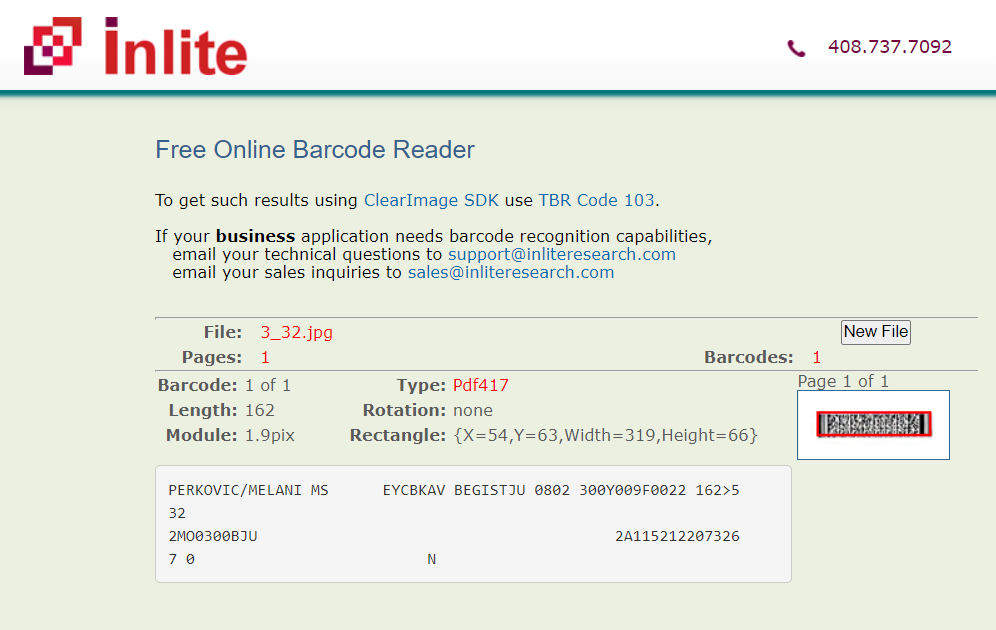
The scanner shows:
PERKOVIC/MELANI MS EYCBKAV BEGISTJU 0802 300Y009F0022 162>5
32
2MO0300BJU 2A115212207326
7 0 N
It’s information, but to know what it represent, I when to this website and realized that each field has its format and significance. To get the flight codes: Airline codes
I wrapped up the information from the actual pass and got the following fields and data:
Format : PE
Name: RKOVIC/MELANI MS (girl)
Booking ref: EYCBKAV
Flight: BEGISTJU
From: BEG - Nikola Tesla Airport, Belgrade, Serbia
To: IST - Istanbul New Airport
On: JU - Air Serbia
Flight N: 0802
Julian date: October 27
Cabin: Y (Economy)
Seat: 009F
Sequence: 0022
Passenger status:1
Size: 62
Version num: 5
With that information we can build up the flag:
GrabCON{JU802_Air_Serbia}
Forensic
Tampered
332 In our company we caught one of the employee tampering a file so we took a some backup from his computer and now we need your help to figure few things.
Name of the new file which our employee was tampering. Example : “important note.txt”
Which tool he was using ? Example : random.exe
What was the changed timestamp on the new file? Example : 2001-01-27_23:12:56 (YYYY-MM-DD)
Content inside the file? Example : e977656fea7ea5b9a8887ecf730860af
Example Flag : GrabCON{important_note.txt_random.exe_2001-01-27_23:12:56_e977656fea7ea5b9a8887ecf730860af}
I started by looking into all documents and I saw a file called ConsoleHost_history.txt
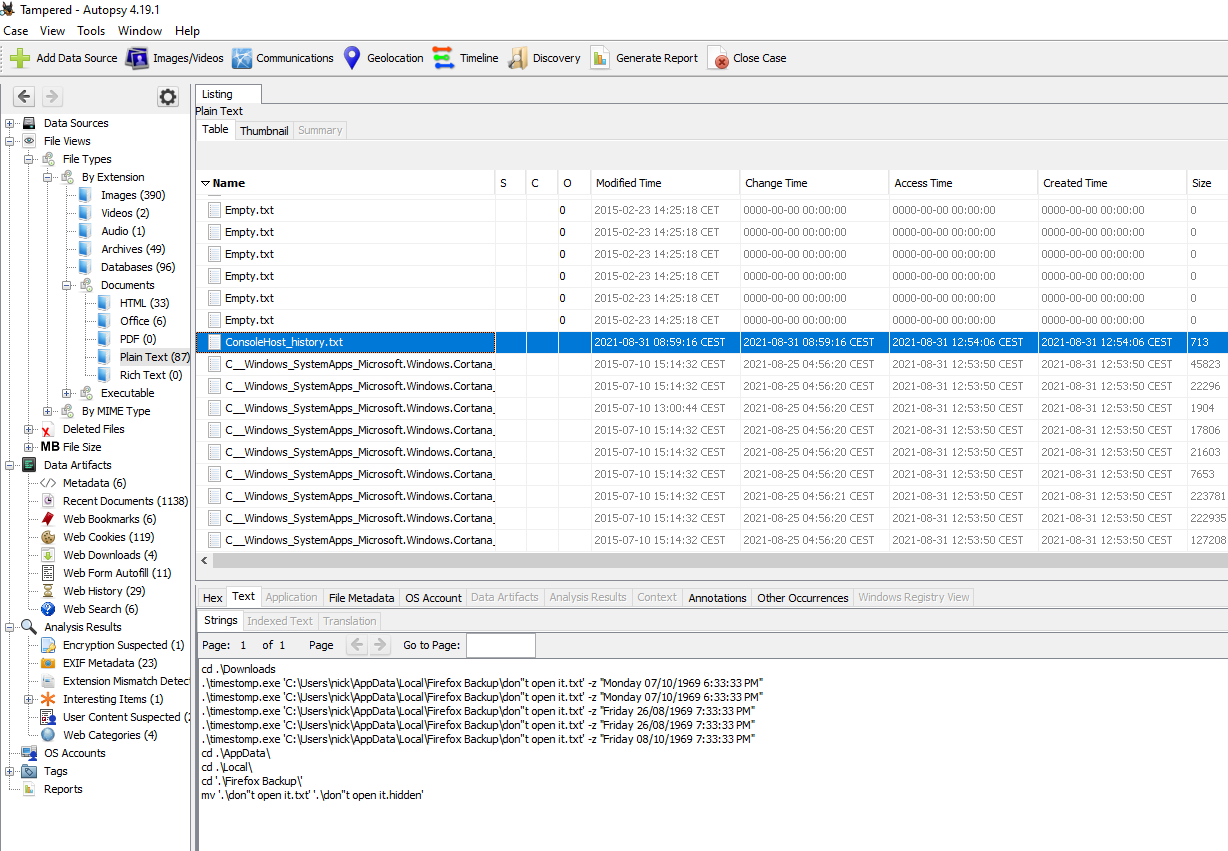
In the file we can see the following commands being executed by the user:
cd .\Downloads
.\timestomp.exe 'C:\Users\nick\AppData\Local\Firefox Backup\don''t open it.txt' -z "Monday 07/10/1969 6:33:33 PM"
.\timestomp.exe 'C:\Users\nick\AppData\Local\Firefox Backup\don''t open it.txt' -z "Monday 07/10/1969 6:33:33 PM"
.\timestomp.exe 'C:\Users\nick\AppData\Local\Firefox Backup\don''t open it.txt' -z "Friday 26/08/1969 7:33:33 PM"
.\timestomp.exe 'C:\Users\nick\AppData\Local\Firefox Backup\don''t open it.txt' -z "Friday 26/08/1969 7:33:33 PM"
.\timestomp.exe 'C:\Users\nick\AppData\Local\Firefox Backup\don''t open it.txt' -z "Friday 08/10/1969 7:33:33 PM"
cd .\AppData\
cd .\Local\
cd '.\Firefox Backup\'
mv '.\don''t open it.txt' '.\don''t open it.hidden'
That filename definitely looks suspicious, doesn’t it? We have the file don’t open it.hidden that was a parameter for the program called timestomp.exe. Those could be parts of our flag. Let’s try to get its content by searching for its name:
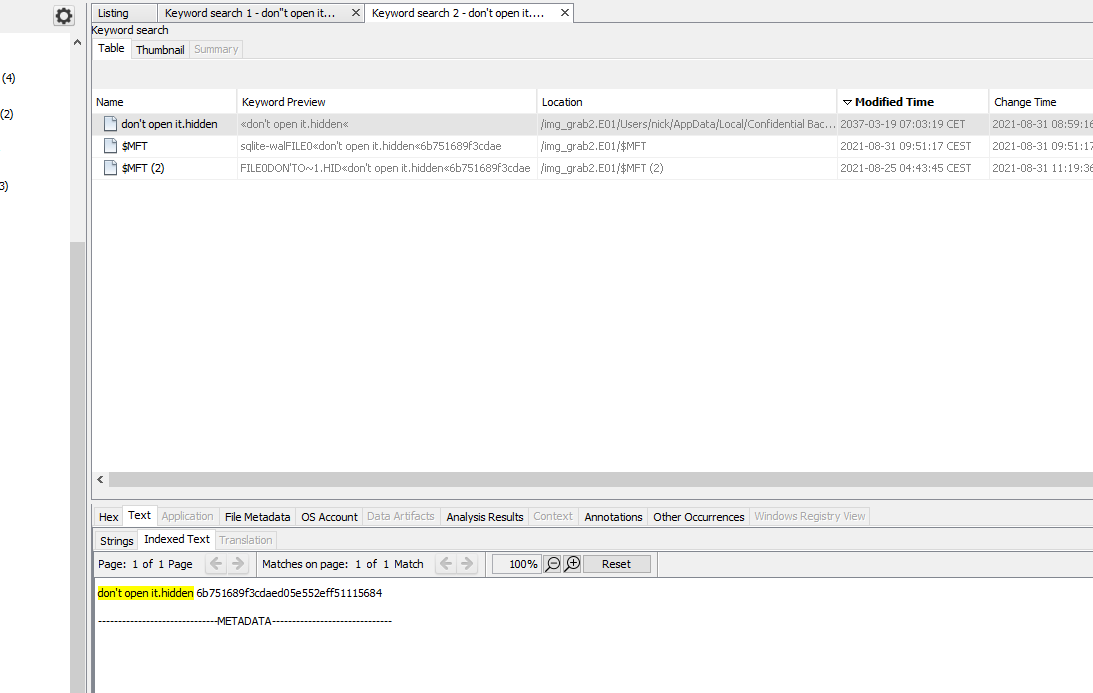
We have the content: 6b751689f3cdaed05e552eff51115684, now let’s get the time
We also have the Master File Table (MFT) in the hits for the filename, we can use them to retrieve the timestamp. For that I made a couple searches on Google and found the following article by SANS and they were using dkovar’s MFT analyze tool:
python2 analyzeMFT.py -f MFT -o output.csv
Then I opened the output from the tool in csv and parsed it on Excel to extract the modification date 10/08/1969 16:33:33:
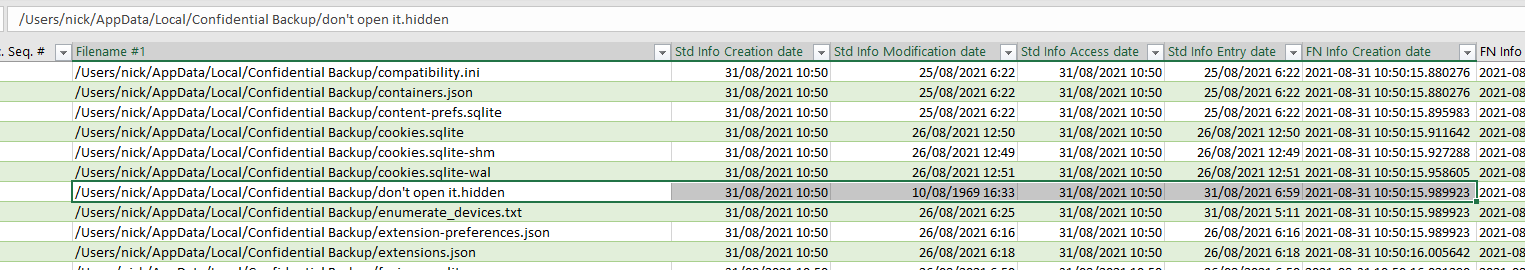
We can now build up the flag, replacing the spaces with underscores:
GrabCON{don't_open_it.hidden_timestomp.exe_1969-08-10_16:33:33_6b751689f3cdaed05e552eff51115684}
Confession
497 Our Employee finally realized his wrong doings and he confessed that he was going to attack the company infrastructure from a remote computer we need you to further investigate this matter and figure out what was he doing on the remote computer.
Note : Challenge File is same as Tampered Challenge.
Since I got the Tampered challenge and I couldn’t make volatility to work for the other challenges, I try myself on this one. I kept working on Autopsy and searched for different tools for remote conections such as Teamviewer, Anydesk, etc.
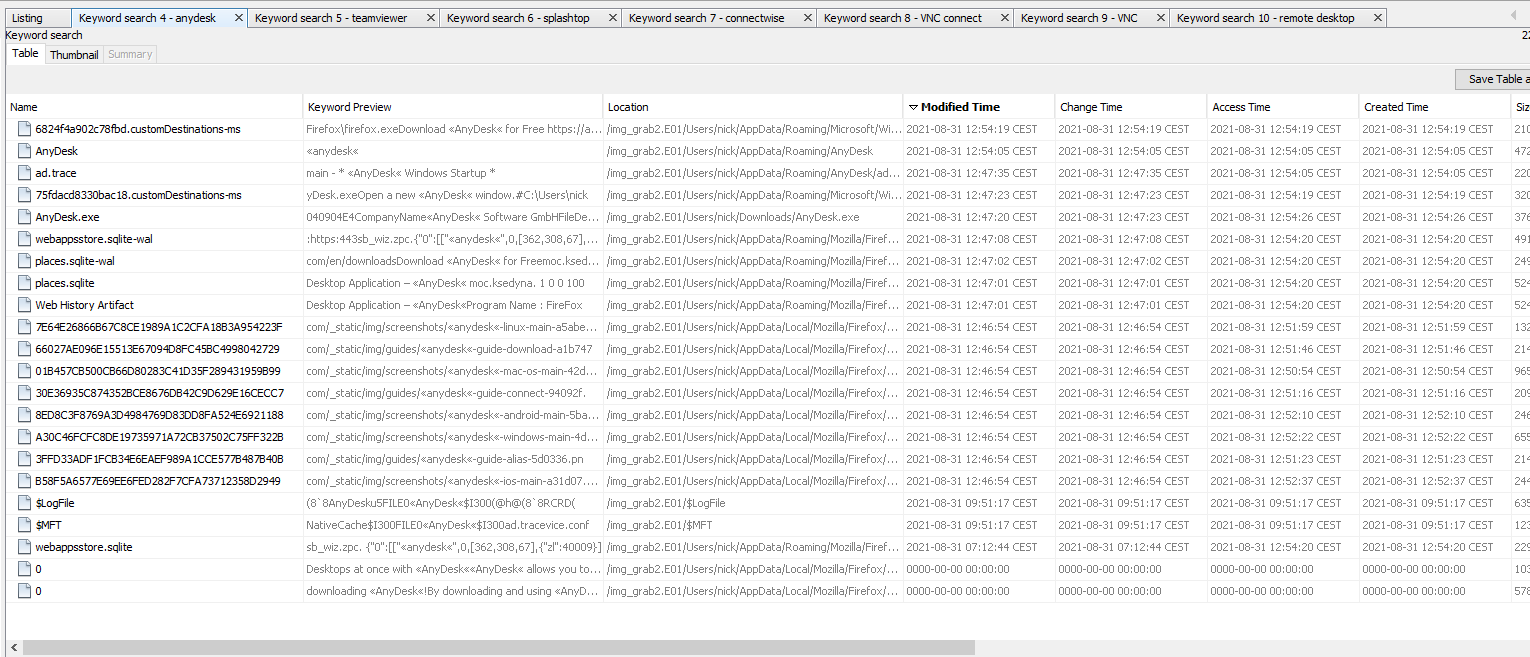
We can see that the user has various applications downloaded and exe files from Anydesk, TeamViewer and Remote Desktop. At this time I was looking for DFIR techniques over the three apps, and I remembered a challenge writeup from previous year TJCTF featuring redpwn team. In there, they used volatility to extract images from the Remote Desktop cache to solve a puzzle with the bitmap (.bmc) files. They didn’t finished the writeup but this posts has an outstanding explanation on it.
The cache is located in the following user path: /img_grab2.E01/Users/nick/AppData/Local/Microsoft/Terminal Server Client/Cache/
Now we have to parse the bmc files, for that there are tools such as BMC-Viewer in Windows or bmc-tools. BMC Tools is a simple python script so let’s use it. I exported the Cache files to Kali and execute the tool over the directory:
kali@kali:~/Desktop/CTFs/GrabCON/Forensic$ python3 bmc-tools.py -s cache/ -d results/
[+++] Processing a directory...
[===] 1062 tiles successfully extracted in the end.
[===] Successfully exported 1062 files.
[===] 1052 tiles successfully extracted in the end.
[===] Successfully exported 1052 files.
[!!!] Unable to retrieve file contents; aborting.
Great! We have a thousand small images. I can see some traces of pastebin, and also from the flag:
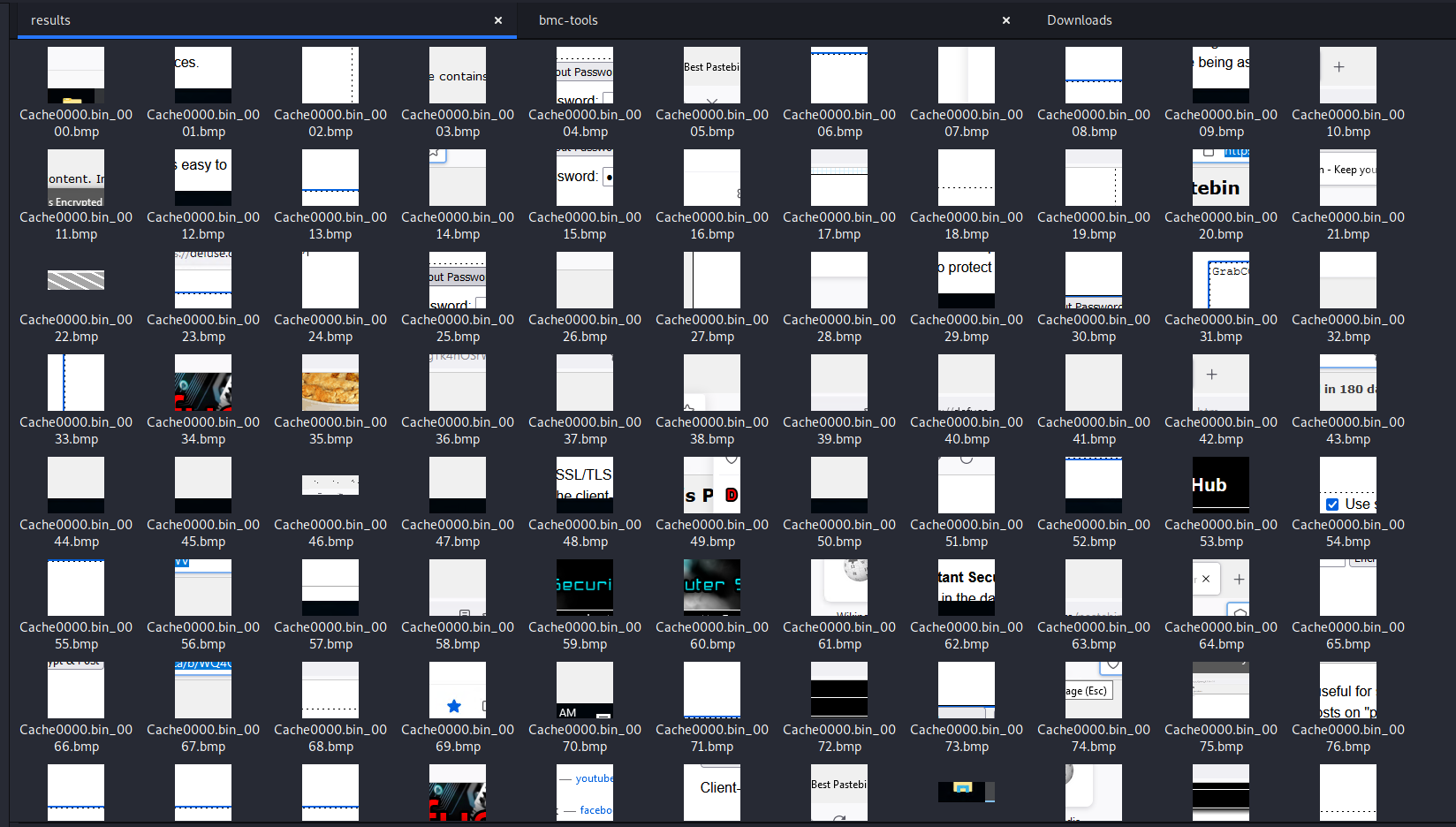
I manage to get some of the fragments:
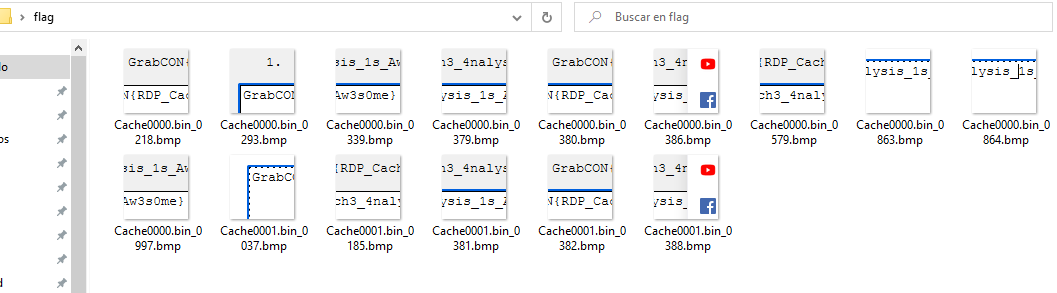
And to order them in Paint xd:
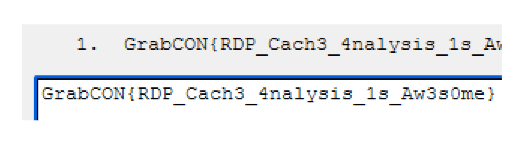
GrabCON{RDP_Cach3_4nalysis_1s_Aw3s0me}
Web
E4sy Pe4sy
100 Hack admin user! Link
A website login and a SQL inyection:
admin
' OR 1=1 #
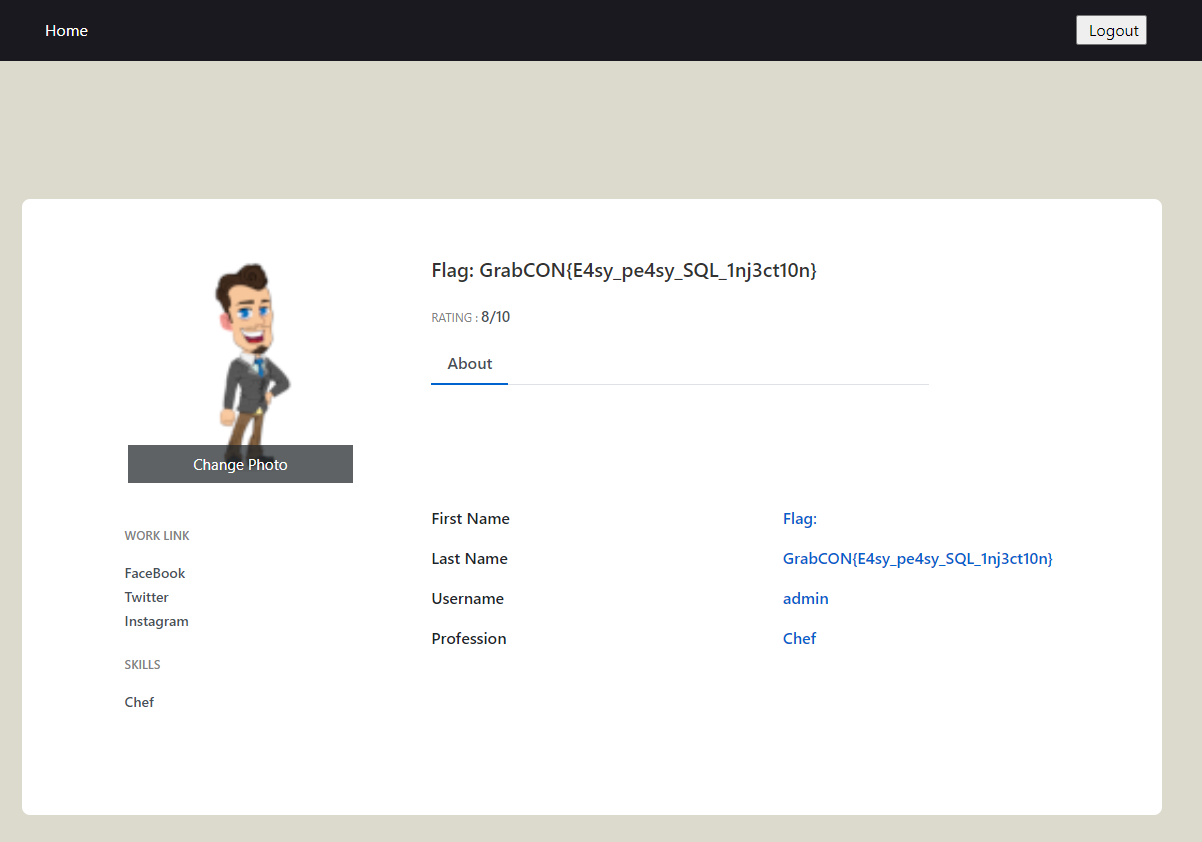
GrabCON{E4sy_pe4sy_SQL_1nj3ct10n}
Crypto
Warm-up
50 Mukesh used to drink and then smoke 5 times a day. He is now suffering form cancer his drink was 64 rupees and 32 rupees cigarette that costs to cheap for him. And he has this much of cancer now.
S01ZRENXU1NJVkhGUVZKUkpaRkZNMlNLSTVKVENWU0xLVlZYQVlLVElaTkVVVlRNS0pIRkc2U1dKVkpHV01LWEtaQ1VVVENXTlJORlNVS1dOUkdGS01EVUs1S0dXVlNLS1pDWFFUQ1ROUllFT1VUTE1STFZDTUxFSk5MR1c0Q0lLWVlEQ1RDWEtWMkZNVjJWTkJKRk1SS09MQktHV05EWktKV0U0VlNOTlJTRVdWVEtLSkxWR01CUklOTEdXNUNQS05XRkVSQ1dLWkhFSVVaUk9CTUZFMjJXS1ZKVENXU0tLWlZWVVJTVUdGTEZLVkNGR0ZIVTRSU1ZQRkdXWVRTTUtOVlRLVEtTR0ZSVEFVSlFNUkdGSVZUTUs1SkZNVExaS1pWWElWMk5OTkxFNFZUS0pKTFZJUkxRSlZKR1dNS1RLTVlEU1RDVk5OMkVRVjJXSlpLRk1WTFVKTkpUQ1VTRUtaV0U0VjJTR0JORklVU1dNUkxGTVJMVUpSSldXNkNYS0lZVlVSQ1RHQVlVT1ZDRk1STUU0VktPS0ZKVENTU0VLWldGTVZLUkdGU0U2VkxMTVJNVktNS1dNRktXV09LREtFWUZVVUNWTk4yRVFVWlJPQkdGTVJLT0s1S1RBM0NNS0pWWFFTQ1hLWlNFSVZMTE1SRFZJMjIySlJMR1dUU0hLSVlWVVMyV05OU0ZHVTMySkpGRksyM0VLVklWTVVTVUtSS1hJVDJXR0JORk1WTDJKSk1GRU1DMktOTEVLUlNXS05XRU1VQ1JOTlNFT1ZEMkpGNUZPVkxMR0ZKVEFXU09LWVlVNFJTVEdGWUVJVlJRTlJKRTIyWlZKNUtHV05LR0tWTEZVVkNXTk00VUdVM0xMSkZGSzIzWUtKSldXU1NMS0lZV0dNS1JHRkpFWVZMTEpaTVZLVlNPSlJLVEE1Q1NLNUtWRVZDV0tWSEZNVVJRSVVZRk0yMkdLWkpXVVZTSktaS0RBT0tRS1FZRFNVQ1JIVTZRPT09PQ==
As showed in the challenge description, we can guess that it’s (base64 + base32) * 5
GrabCON{dayuum_s0n!}
Cool CTF! I didn’t have all the time I wanted to spend on it and also had issues with the volatility3 that drove me crazy. Thanks to my team and specially RazviOverflow who threw some light on the OSINT challs ;)
Thanks for reading!

